The Internet, something that we all think we know. We think we know how it works, what all is on the internet and the uses of it. I mean, we use it every day, shouldn’t we know all about it? However, you may not know as much as you should about the internet. The truth is, the internet that we use only makes up about 4%. Yes, this includes all our social media, search engines, and gaming sites. You may think that these websites are so big, why do they only take up so little of the internet? This is because the for rest of it we do not have access. The other 96% is known as the deep web and the dark web. This is where business and government agencies have their information. The reason why the deep web is so large is because of how extremely large business and government data bases are. They span several years long and an incredible amount of data in them. However, a small part of the deep web is the dark web. On the dark web, there is more sinister items stored there. In this post we will look at both the deep web and the dark web respectively. Will see what kinds of threats come from both. We will look at how we must be more aware what we share on the internet.
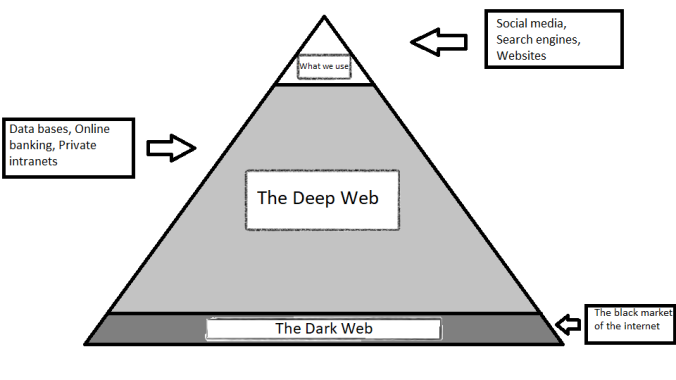
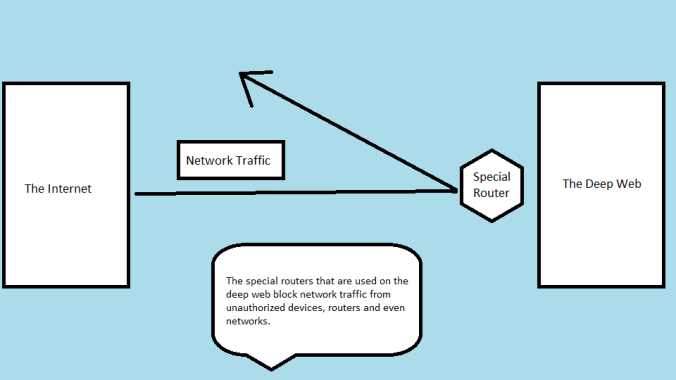
We will first talk about what the deep web is all about. As I said before, this part of the internet is inaccessible to you and me. This part of the web cannot be indexed by regular search engines or methods. This is where big companies like IBM and Google store all their data. It is estimated that 54% of the world’s data bases are stored there. The deep web also holds private intranets for colleges and universities. These intranets hold private message boards, personal files and so on. It is estimated that these take of 13% of the deep web. The deep web also includes online banking, video on demand and email applications. It may seem like you do have access to things while using a browser, but you don’t. The only way you have access to these places is that you have a password and user name that accepts you onto the private network. You cannot have access without these things and just get on and see the information. This brings us to how these places can be hidden from people on the internet. These sites on the deep web use special routers. These special routers reject traffic that is coming from an unauthorized device, or the device does not meet certain requirements, or they do not present the correct user name and password assigned to that device. Another way these places stay hidden is with private intranets. These networks are only accessible at a certain site or you must have login information to be able to join.
The darker part of the deep web is called the dark web. The dark web is inaccessible to you and I like the deep web, but it uses different methods to stay hidden from the public. The dark web is like the black market of the internet. This is where people sell drugs, credit card numbers, social security numbers and much worse. These sites use something called an onion router. The onion router works only with other onion routers. The routers are all over the world and the owners are unknown. These routers are accessed by special search engines. These search engines will use strong encryption software so that transmissions are secure. The dark web is most likely the place where stolen data ends up. Like mentioned before, people will sell this stolen information to the highest bidder. This is yet another reason why we must protect our data.
As we roam the internet, we must be careful of what we share. The internet is a big place and it is ever- expanding like our universe. So, as we spend hours on social media or visiting different sites, we must realize that we never know where our data will end up. Maybe they will go into a large data base where a company is collecting data to see what trends young people present the most or, it could fall into the hands of a person who will impersonate you to get even more of your personal information and sell it on the dark web. As we go through our day to day lives, we must always be cautious of who is lurking in the shadows in the real world and the cyber world.
Interested in discussing the challenges and solutions on this topic? Please contact us at bizdev@sdsolutionsllc.com or call 540-860-0920.